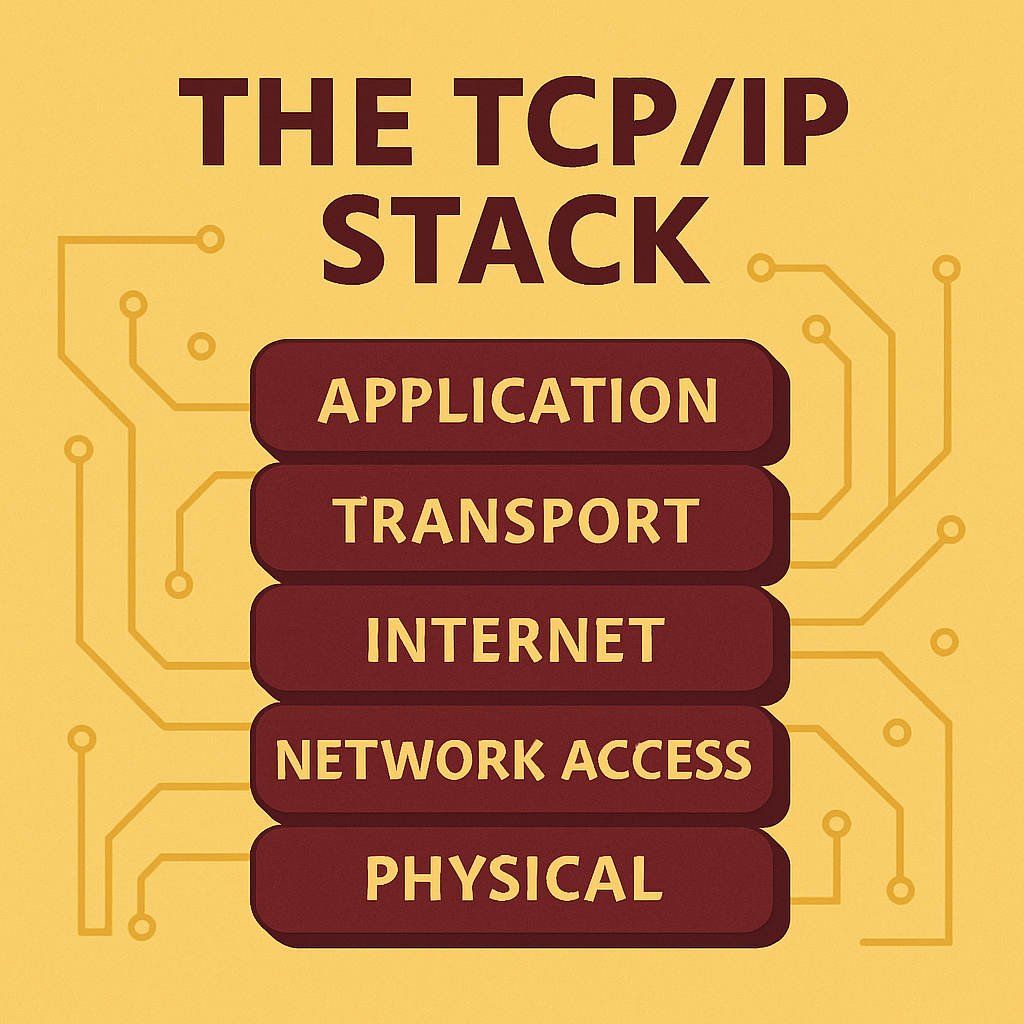
TCP/IP, short for Transmission Control Protocol/Internet Protocol, is the foundational suite of protocols that defines how data is transmitted across interconnected networks, including the Internet. It's not a single protocol, but a structured set of layered protocols that handle everything from application level communication to physical data transmission.
Historical Development
Originally developed in the 1970s by the U.S. Department of Defence, TCP/IP was designed for resilient, fault tolerant communication between heterogeneous computer systems. It became the standard for ARPANET internet's early predecessor and was formally adopted for all internet-based communication in 1983.
Universal Structure
The importance of TCP/IP lies in its universality and structure. It enables information to travel from one application on one machine to another application on a different machine across routers, switches, cables, wireless links, and different operating systems. It ensures the addressing, packaging, delivery, and verification of data.
Complete Communication Model
Unlike isolated protocols like TCP or IP alone, TCP/IP is a complete communication model. It handles:
- Data formatting at the application layer,
- Reliable transport at the transport layer (via TCP or UDP),
- Routing and addressing at the internet layer (via IP), and
- Physical transmission over network media.
Whether it's loading a webpage, sending an email, or streaming a video, TCP/IP is the framework that makes it all work efficiently, reliably, and at scale.
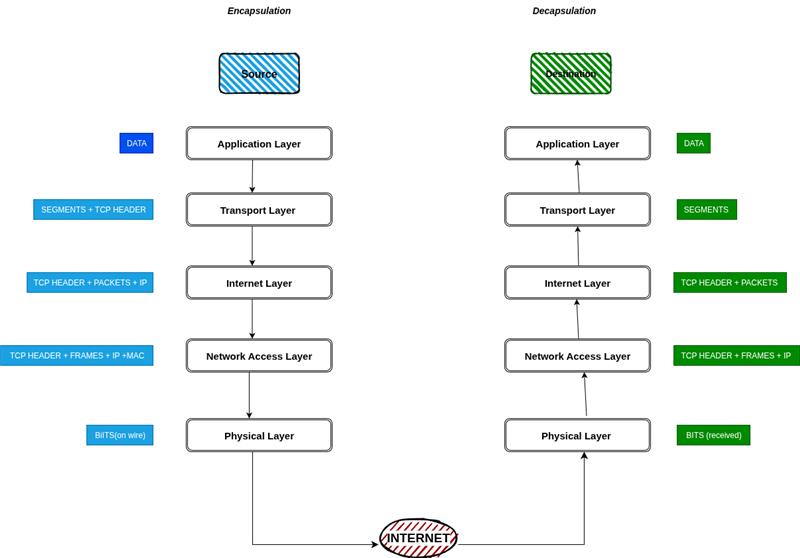
TCP + IP Synergy
Using TCP with IP creates a system where:
- IP finds the destination.
- TCP ensures the message is delivered completely, in order, and without errors.
This combo gives us:
- Reliable file transfers
- Accurate web page loading
- Functional remote logins
- Resilient, end-to-end communication over unreliable networks