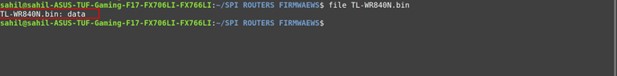
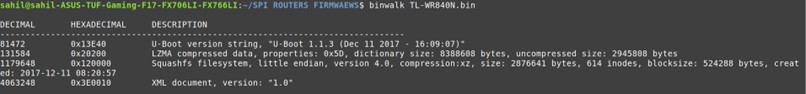
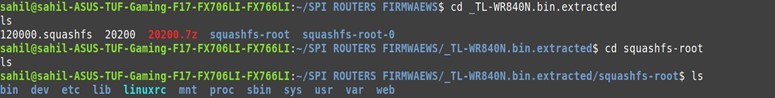
Before doing any advanced analysis, we identify what type of file we're dealing with using the file command:
File Classification:
file TL-WR840N.bin
This gives us a basic classification whether it's just data, a compressed archive, or contains a known file system like SquashFS. We'll need deeper inspection to understand its structure.